zIPS Protection
zIPS Mobile Intrusion Prevention System – Revolutionary Network, Mobile Device & App Security

zIPS Protection
zIPS Mobile Intrusion Prevention System – Revolutionary Network, Mobile Device & App Security

Zimperium’s zIPS™ is the world’s first mobile intrusion prevention system app that provides comprehensive protection for iOS and Android devices against mobile network, device and application cyber attacks.
Much like a doctor can diagnose an illness by analyzing the symptoms your body is exhibiting, zIPS™ can detect both known and unknown threats by analyzing the behavior of your mobile device. By analyzing slight deviations to the mobile device’s operating system’s statistics, memory, CPU and other system parameters, z9™ detection engine can accurately identify not only the specific type of malicious attack, but also the forensics associated with the who, what, where, when, and how of an attack occurrence.
Zimperium developed the innovative and award-winning z9™ engine by training it over many years on proprietary machine-learning algorithms that distinguish normal from malicious behavior on Android and iOS devices. Unlike cloud-based mobile security solutions that employ app sandboxing or tunnel traffic through the cloud, the z9™ engine sits directly on the mobile devices within the zIPS™ app, in order to provide complete protection around the clock.
Uses the on-device z9™ detection engine to monitor the whole device for malicious behavior, and to dynamically detect known and unknown threats in real time.
Leverages machine learning to analyze deviations to device behavior and make determinations about indicators of compromise to accurately identify specific types of attacks and classify zero-day attacks.
Implements quick incident-response recommendations and decisions when malicious activity is discovered.
Leave your employees to their own devices. zIPS™ accommodates the human factor. We secure iOS and Android devices in real time without compromising the user experience or violating a user’s privacy.

You can secure your enterprise from breaches occurring in BYO environments by using the only advanced threat protection that was specifically developed for mobile devices. Based on a disruptive, on-device detection engine that uses patented machine learning algorithms, zIPS™ protects the entire mobile device — not just mobile applications — from multiple attack vectors.

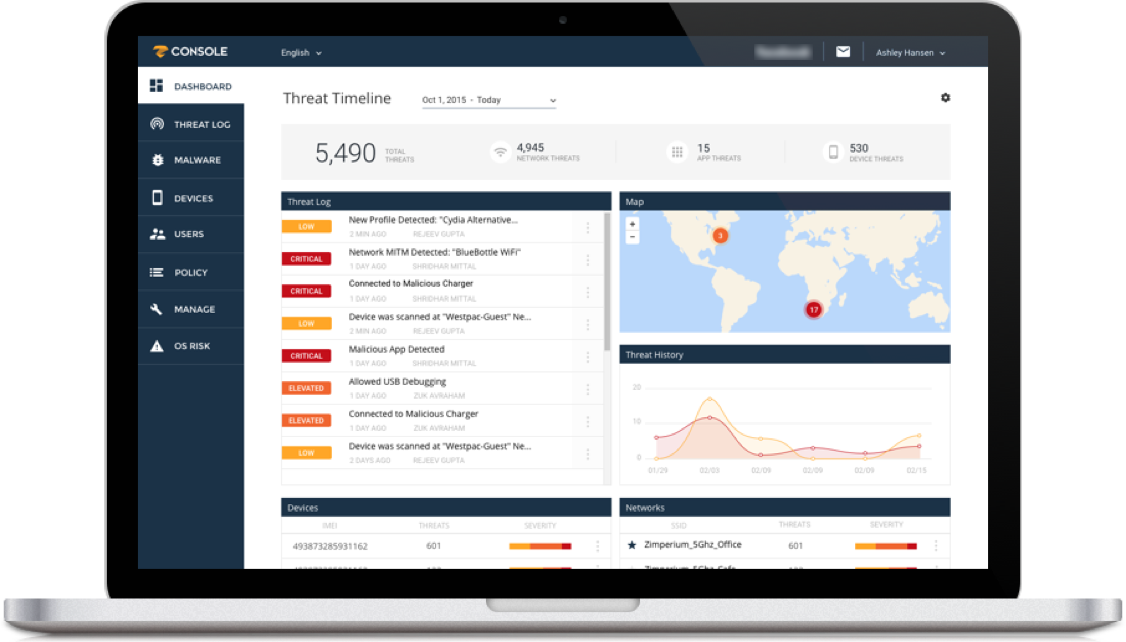
zConsole™ is an enterprise mobile threat management console that provides security teams with visibility across all mobile devices in the organization to assess enterprise risk, identify security gaps and update policies to improve mobile device and application protection. Comprehensive dashboards and detailed reporting make it easy for Security Administrators to manage risk and monitor incidents on zIPS™-protected devices.
Incident Response teams can take advantage of unparalleled mobile threat forensics for analysis and action to prevent a compromised device from turning into an outbreak:
to understand the threat and the changes made to the device, including various types of OS information and persistent modifications
details on cell and Wi-Fi networks, current and ongoing connections, as well as other contextual information to profile the attack and help identify the source
details on detected malware samples
zConsole™ enables the centralized management of all zIPS-protected endpoints:

zIPS provides users with information on nearby Wi-Fi networks and their potential risk. By evaluating potential risks on nearby networks via a map view, users can determine which network they should avoid and which ones have not detected malicious activity or hacking. If a user does connect to a potential high-risk network or zIPS detects a network attack, the user receives an alert and a recommendation to disconnect from the network. The threat detection information and risk profile is then provided to other zIPS users to inform users of a new Wi-Fi risk.

zIPS provides users with information about app activity on their device when performing checks on the operating system, network connections and downloaded and installed apps. Users are now able to see an activity summary for the scans and security checks zIPS silently performs on their device so they can quickly and easily understand how their apps, network connections, data and personal information are protected from compromise.
To address enterprise-specific mobile security vulnerabilities, Zimperium also provides a risk-based approach to mobile security management.
z3A™ Advanced App Analysis helps understand the actual risks to your business that are posed by mobile app vulnerabilities. From zConsole, you get a holistic view of your devices’ risk posture, including OS/device, network and app risks.
See how Zimperium z3A™ can help you identify mobile vulnerabilities, and evaluate and mitigate their risks.

Enable Security Administrators to continuously monitor and manage the health of all mobile devices from a real-time threat dashboard with the ability to trigger automated response.

Unmatched network, device and malware forensics data lets security administrators view and understand each mobile security incident, including the who, what, where, when and how of an occurrence.

Define and enact risk-based policies to continuously protect your organization from mobile attacks.
zConsole™ is a cloud-based management console that can be accessed from a browser on any device at any time. You get a clear picture of your mobile threat and risk posture across your enterprise.
In one tool, administrators get an overall view of their enterprise mobile network, device, and application threats. You can view the threat logs, maps and history, top-attacked devices and networks, and where the OS risks lie, as well as specific vulnerability risks. You can also drill down for more detail and remotely protect your fleet of iOS and Android devices.