

It stores network traffic as they are without any loss of data on a maximum of the 40G network.

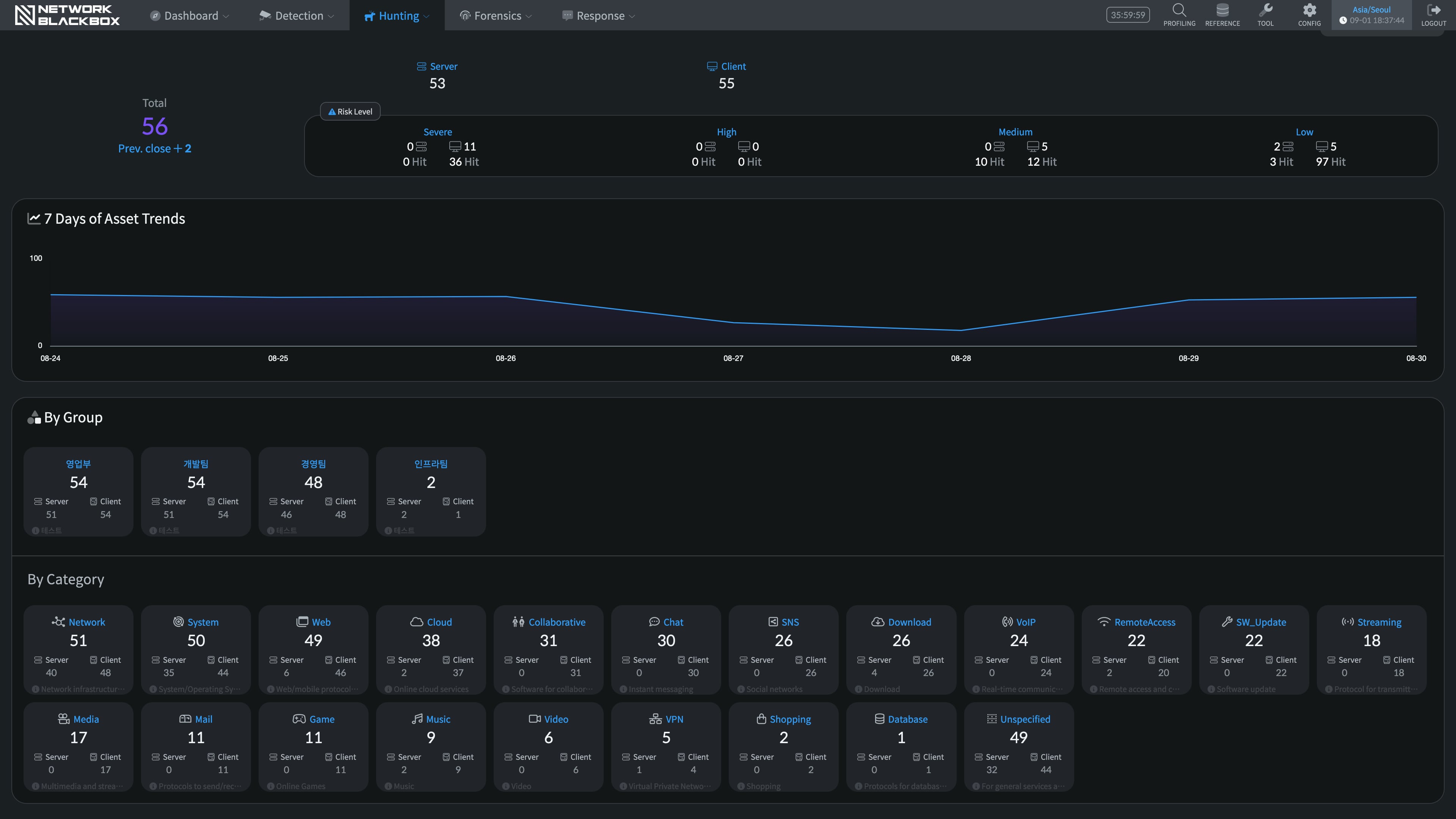
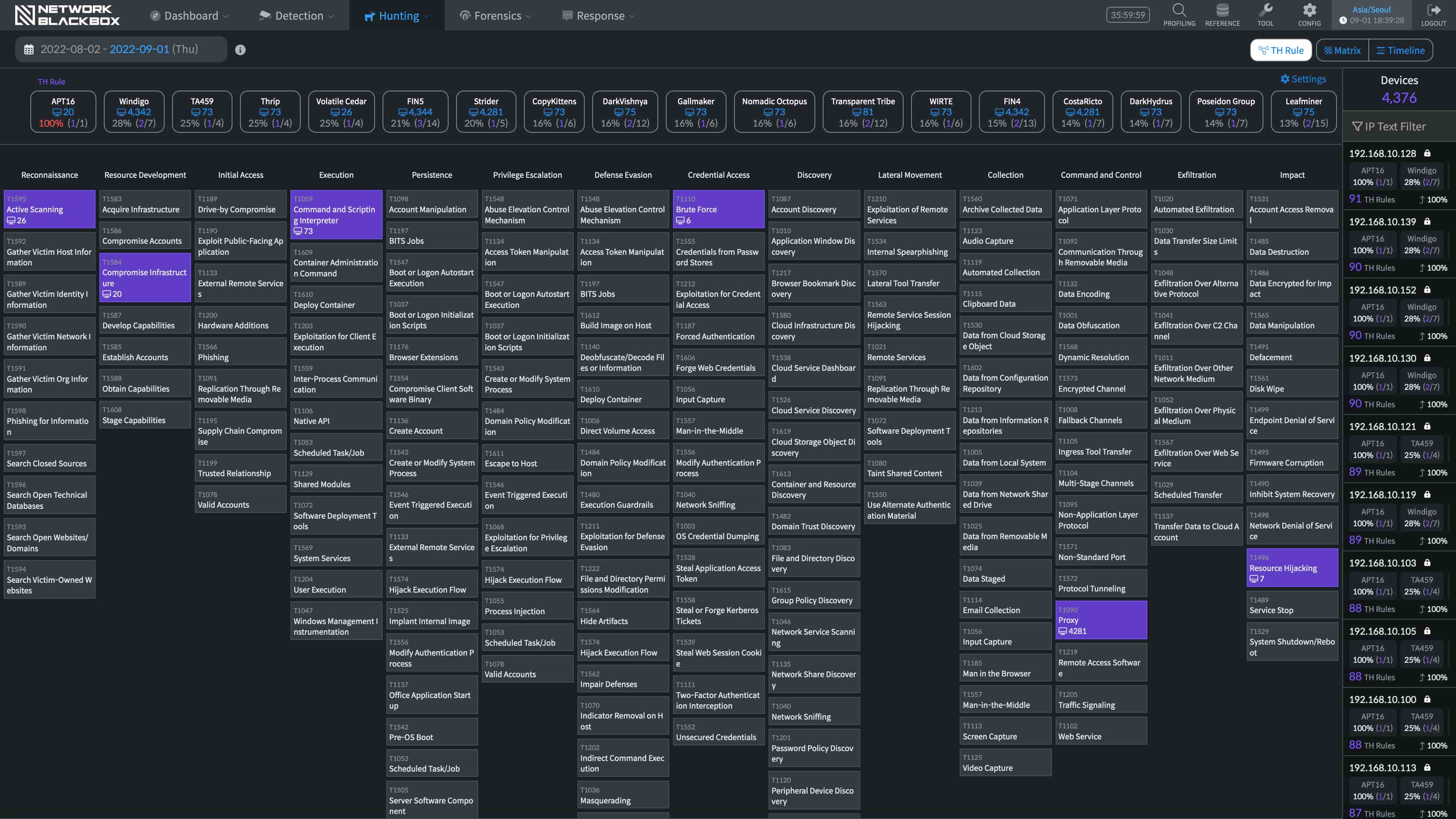
Establish a framework from the TTPs perspective to hunt threats.

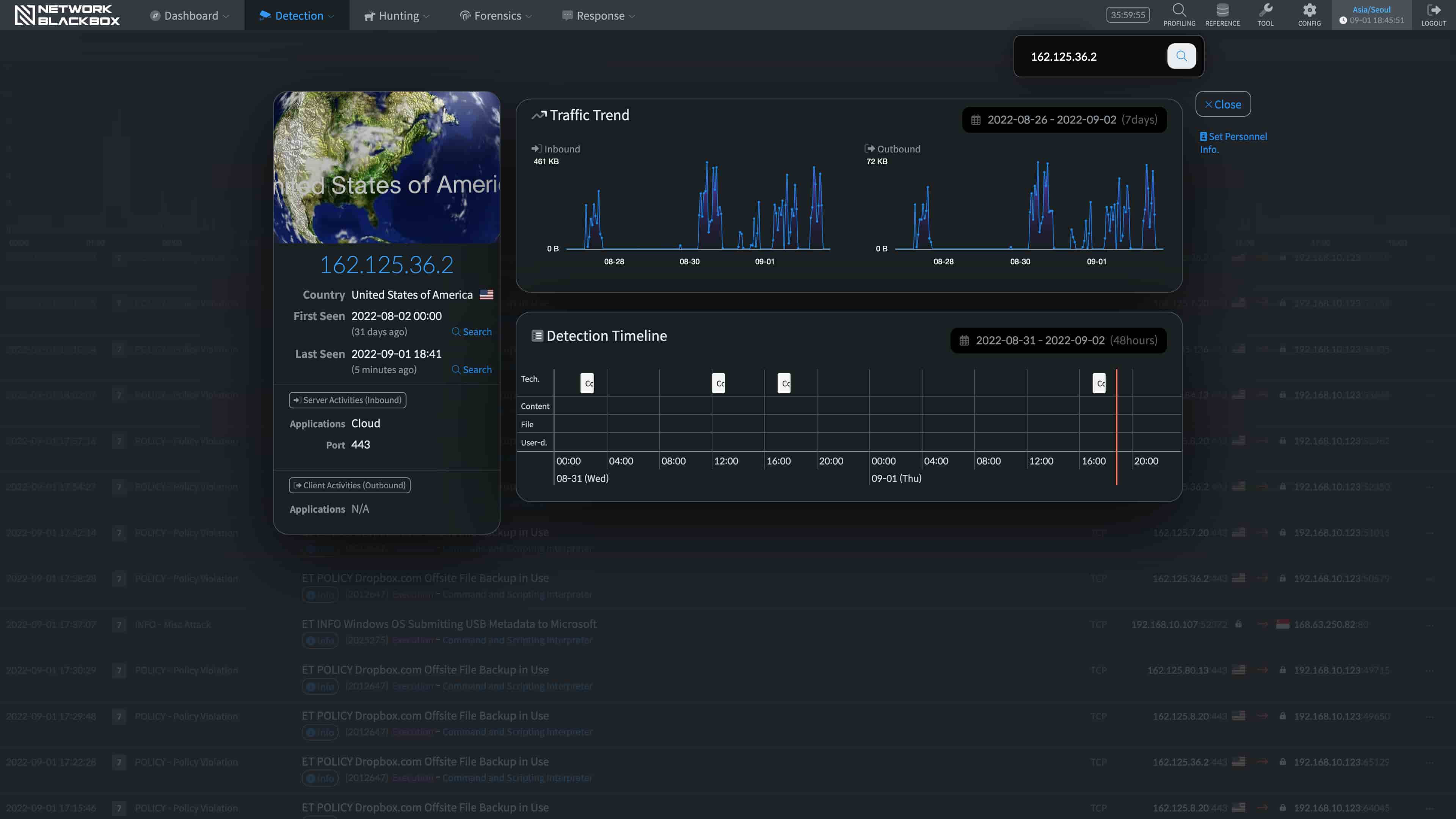
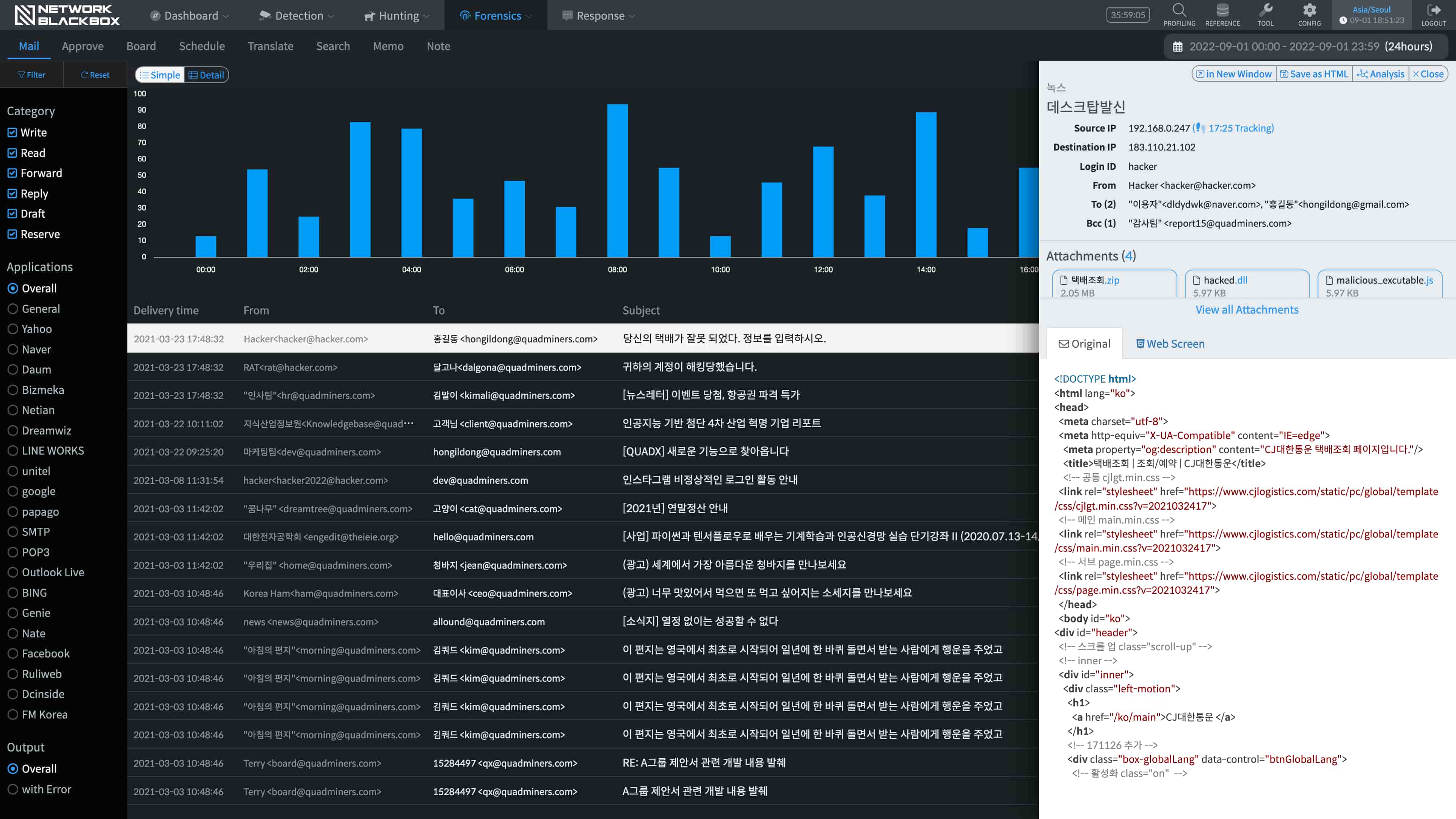
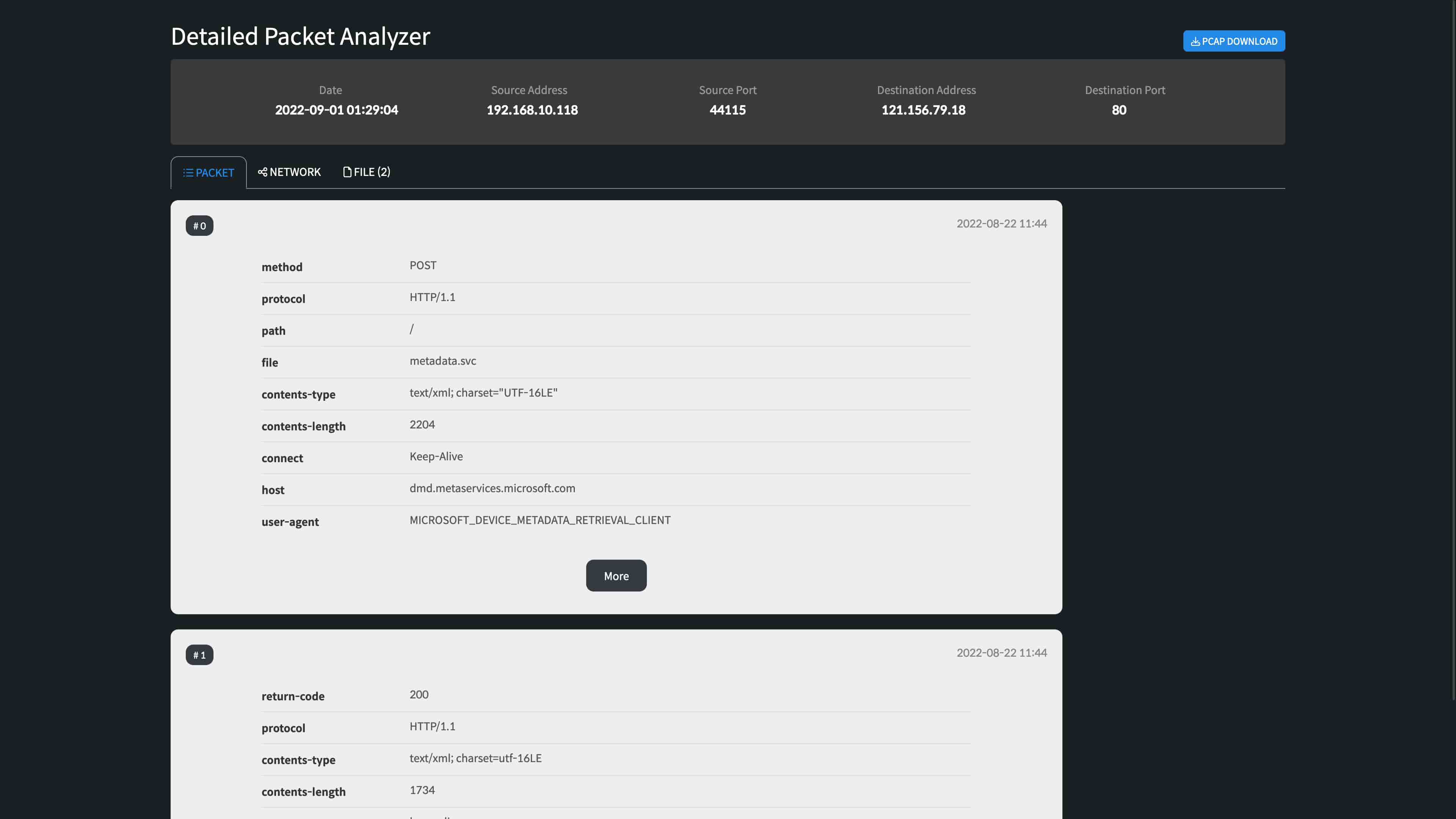
Provides evidence of specific attacks in an infringement accident.

It informs you of the threat actions that have occurred through various channels.
Connectivity
Zero Packet Loss
Save up to 15PB
※ We collect packets using a mirroring method, while there is no impact to the network.
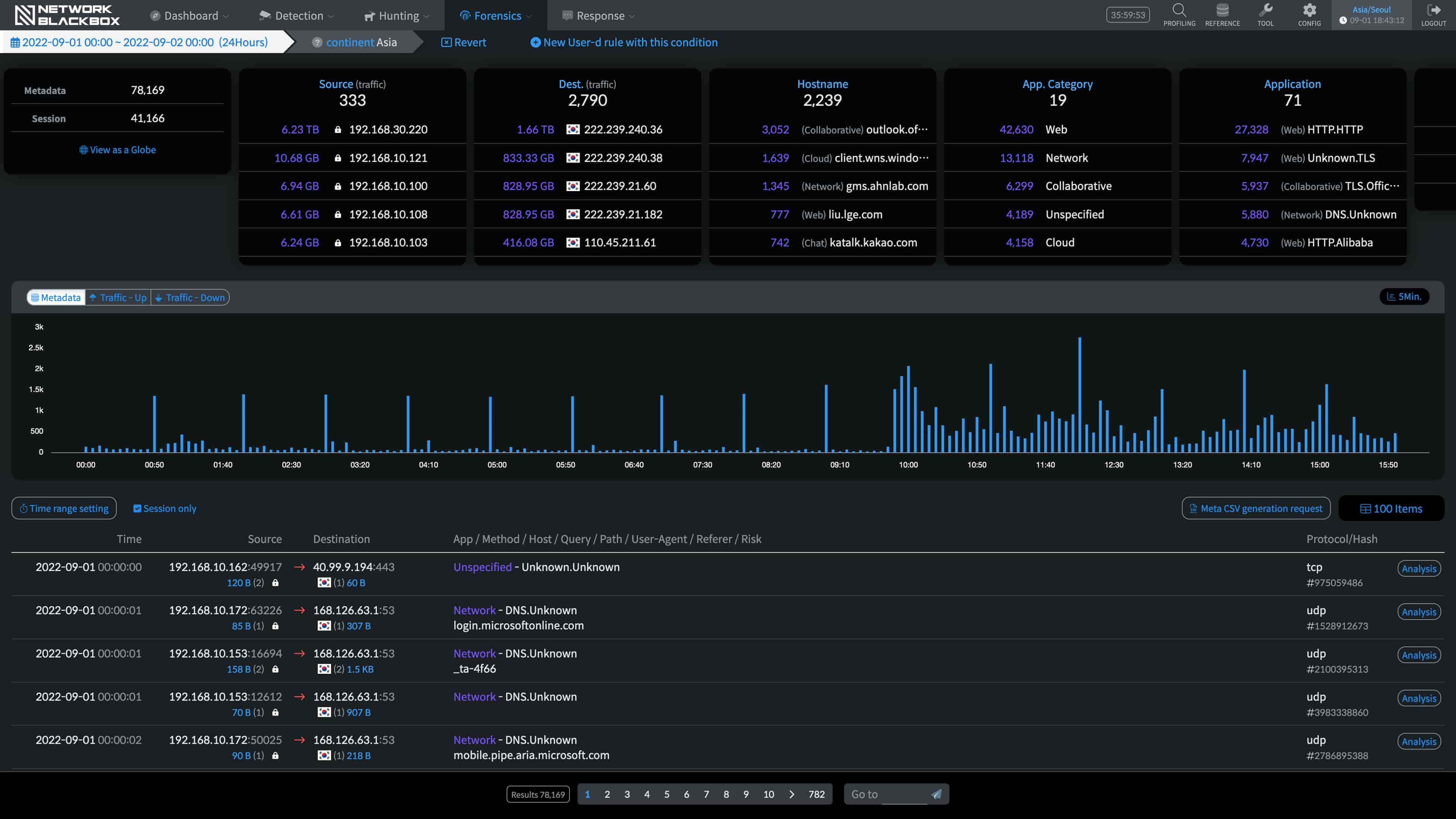
It does not simply store packets,
but instead recombines up to the range of Application Layer (L7) to visualize what’s happening on the network.
※ In addition, it performs various post-processing tasks such as virus scan, detection of abnormal actions, and etc.
It uses the newest threat detection rules to detect unusual signs in real time.
Cyber Threat Hunting
Anomaly Detection
Signature-based attack detection
Behavior-based attack detection
C&C, malware and worm detection
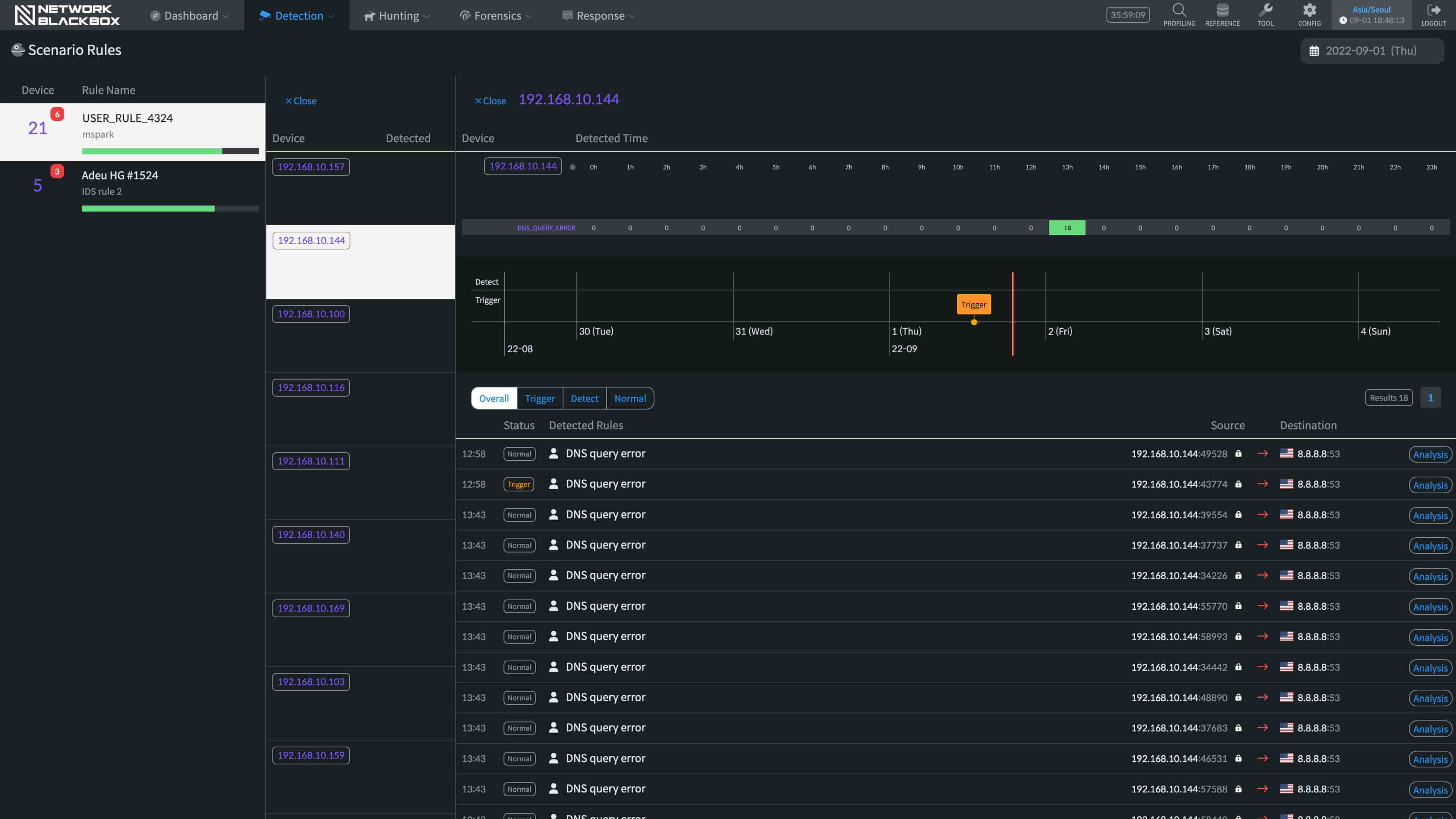
Scenario-based attack detection
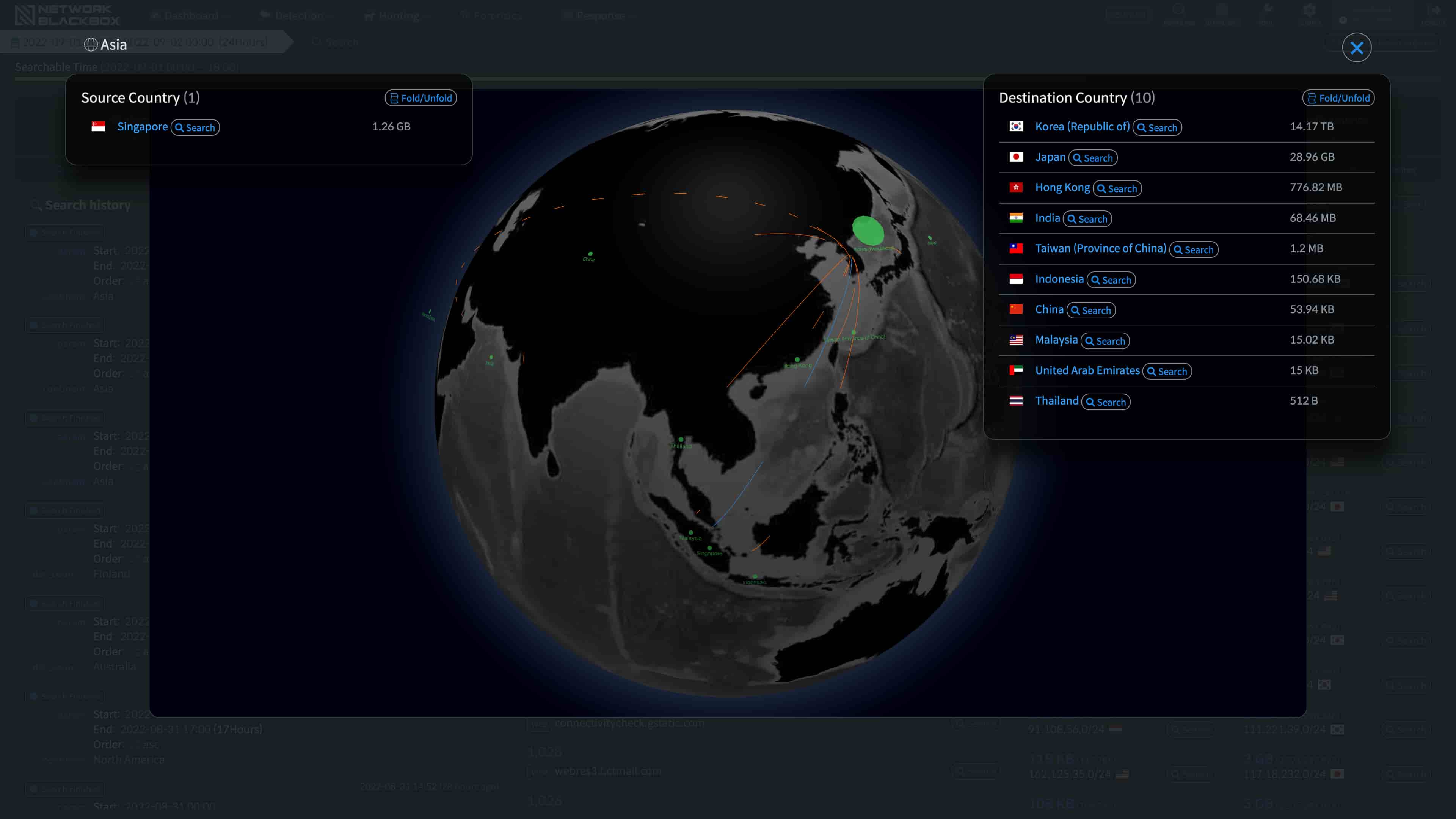
It provides clear visibility malware by analyzing the detected details gathered from various angles.
More than simply analyzing for cyber threats, it checks the actual packets, not just logs, through its highly refined Database.
| Payload | Flow | Contents | Rules | ... | ... |
| Stats | Event |
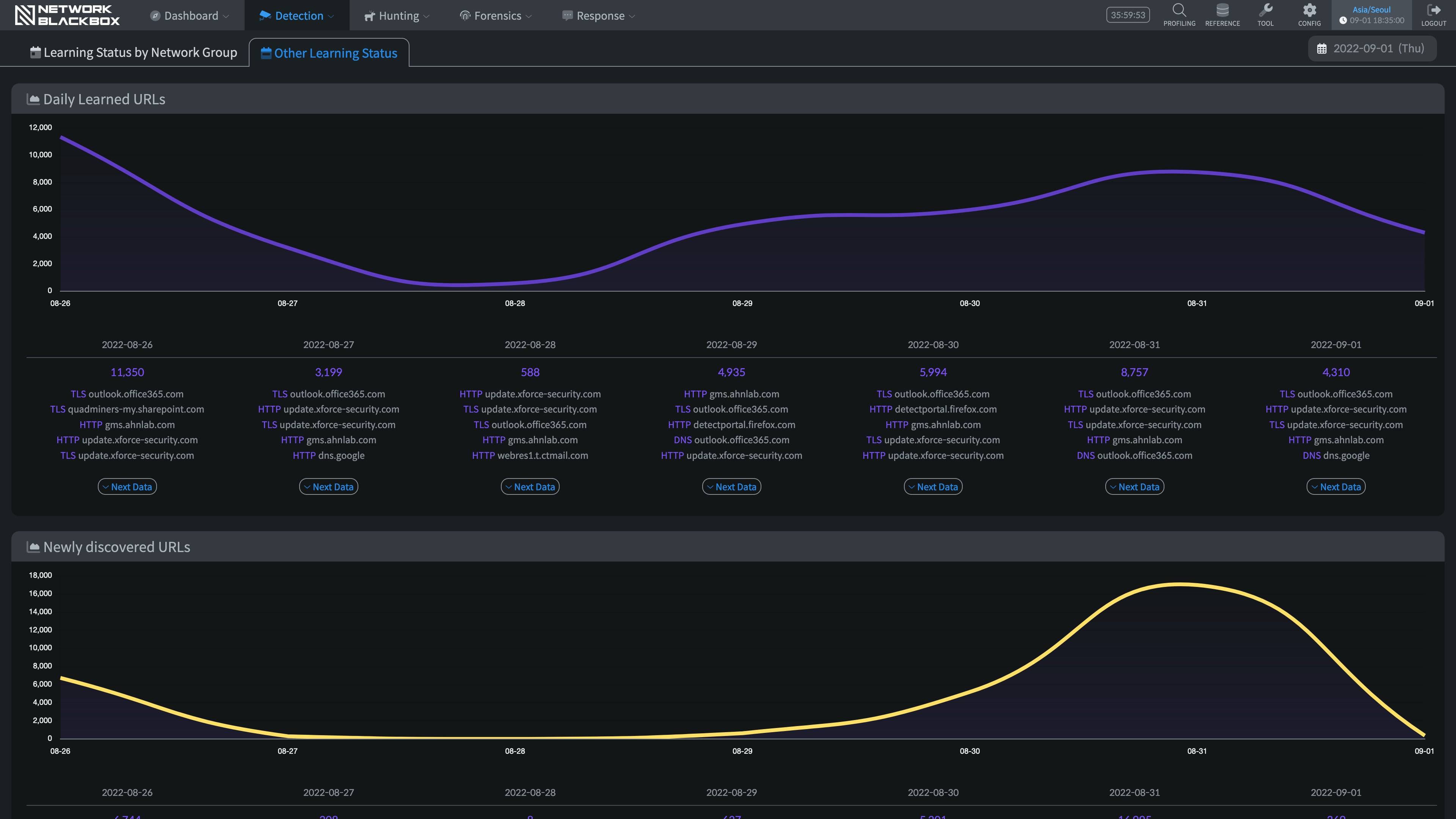
It precisely runs detections by learning detected events as well as various behaviors that occur on the network. It is a machine learning based AI solution that is able to explain reasons and causes of the results.
 GS Certification Level 1
GS Certification Level 1Network Blackbox, a Cyber Threat Security solution has received GS Certified Level 1.
Network Blackbox 3.0
Certification Number 21-0562