
Beyond Security DAST finds code weaknesses, determines a product’s security without access to the source code, and is compatible with most hardware and protocol; including IoT, CANbus, and automotive. SAST checks the code security quality of applications and integrates SecOps into DevOps so your organization can include and streamline security solutions into the CI/CD function. Vulnerability management and assessment can quickly detect threats with the most accurate and fastest possible improvement in network security customized for your organization.
Get a scalable, cloud based, realtime black box fuzzer that doesn’t require source code and has over 250+ prebuilt protocol testing modules.
Designed with simplicity in mind, it inspects both code quality and security together helping reduce your costs with early source code vulnerabilities before deployment.
Our fast and accurate vulnerability management and assessment solution that delivers cost effective, scalable network security scanning.
Easy to implement, Beyond Security scanners can save you time, money, and effort. SAST and DAST can go hand-in-hand when it comes to security. Inspect for code quality and security together, help your IT professionals detect and prevent security weaknesses before a product launches, and realtime scanning for cybersecurity vulnerabilities after deployment.
SIMPLICITY IN MIND
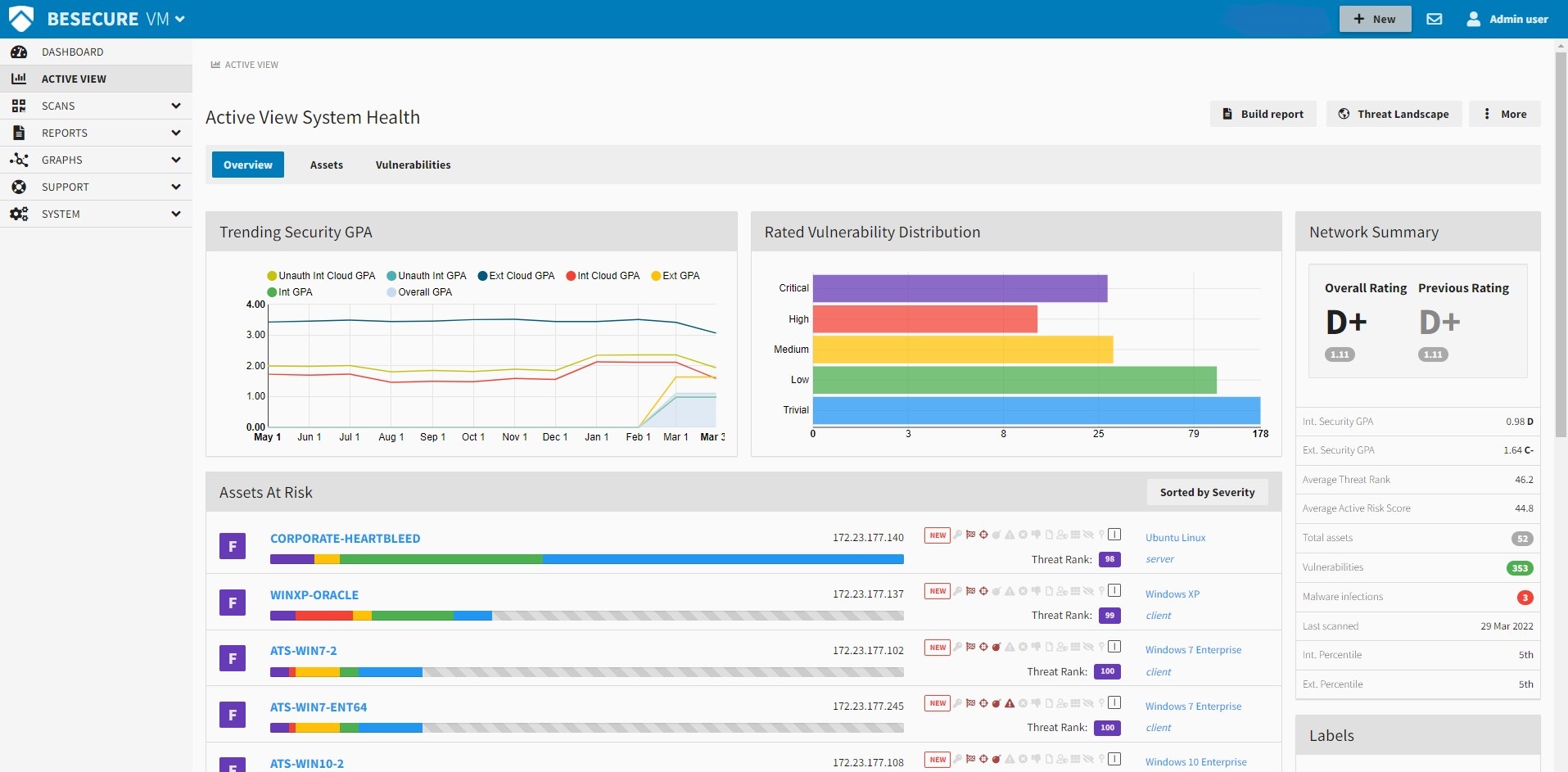
BeSECURE is designed with simplicity in mind and can help any developer get on a fast path to vulnerability security scanning with simple steps.
SAST FROM THE START
BeSOURCE SAST automated source code scanning detects vulnerabilities early in the software development life cycle preventing expensive fixes after deployment.
REALTIME DAST FUZZING
BeSTORM DAST detects realtime vulnerabilities because it doesn’t need access to source code, certifying the security strength of any product, including IoT devices and automotive ECUs.
Automation, scalability, and integrations making security scanning before and after deployment much easier for your IT staff.
There’s a single GUI to learn that includes over 250+ prebuilt protocol testing modules and the ability to add custom ones.
Adhere to all necessary standards, including Common Weakness Enumeration (CWE), SANS TOP 25, OWASP TOP 10, and CERT Secure Coding Guidelines.
Run quick checks during development on new code and perform longer tests after deployment to find security issues.